Showing top 0 results 0 results found
Showing top 0 results 0 results found

One of the benefits of running a small business is the potential to operate it from home. Everything’s within reach, there’s no commute time, plus Netflix is always near. But running a home business means you need greater awareness of security loopholes commonly found in residential premises.
Many of us come from an office environment where everything is pre-deployed. That typically means an IT team has secured the infrastructure. We usually go for ready-to-use setups for home; it’s plug-and-play, convenient, but not exactly the safest.
Here are some of the best little-known security loopholes you need to be aware of (and close) if you’re running a home business.
1. Change your router admin password
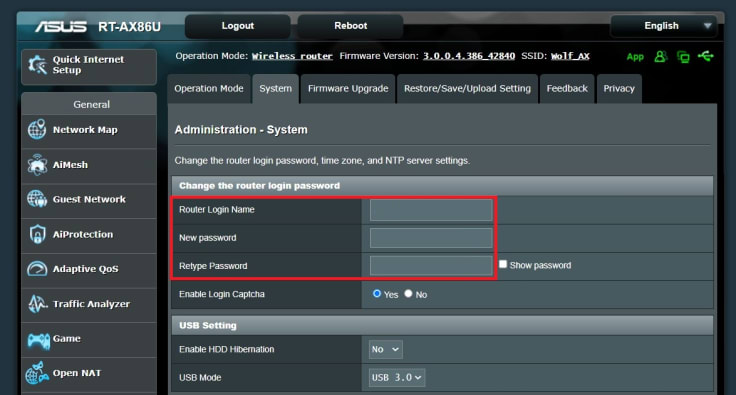
Wireless is everywhere these days, not just on our mobile phones. We often buy wireless routers for home use to handle all of our devices with a single box. These handy devices come password secured, but remember that everyone gets the same credentials.
Make sure you change the administrator password as soon as you’ve plugged in your router. To do this, refer to your router’s setup guide; the process will vary by brand.
2. Secure that WiFi
Unfortunately, WiFi is also notoriously insecure, and you need to make sure that signals are protected to prevent intrusion on your home network. Most modern routers will support various privacy protocols such as Wireless Protected Access (WPA).
I recommend you select WPA2 at least to improve the resiliency of your WiFi network. To do this, log in to your router interface and look for the “Wireless” section. You’ll see a whole bunch of settings; just change the “Authentication Method” to WPA2 and enter a strong password in the “WPA Pre-Shared Key” field.
3. Make sure you only browse secure websites
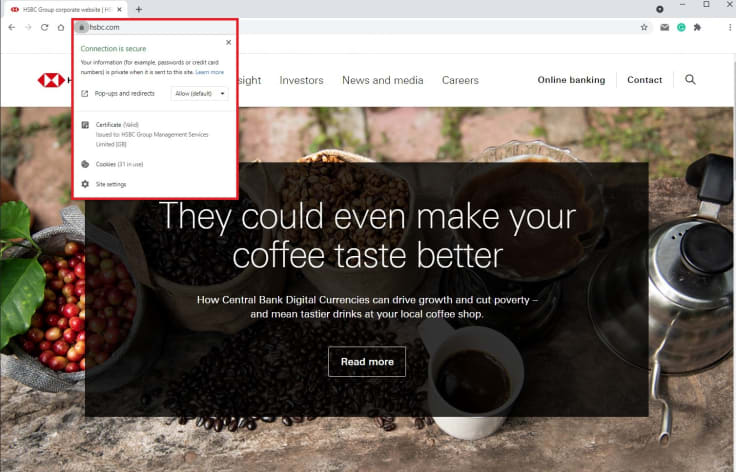
Websites are so numerous today since everyone can set them up easily. The problem is that not all are equally secure. While search engines like Google try to enforce SSL encryption, not all websites have converted to HTTPS yet.
SSL on a website means that all data flowing between you and that website is encrypted. It helps ensure that stealing data during the connection isn’t useful to anyone. Be aware of the website you connect to, and where possible, make sure they offer SSL encryption.
4. Always use internet security software
Running any gear that’s connected to a network is dangerous. So long as there’s access, someone will try and break into your device. To avoid things like this, make sure you use Internet Security applications, not just anti-virus.
Internet Security applications help improve your digital privacy as well since they often block trackers and other malware. Some comprehensive solutions include Norton 360 or Kaspersky Internet Security, but many others are available.
5. Sign up for a virtual private network
A Virtual Private Network, or VPN, can help improve your online security significantly. This is especially true for home business use since you may need to connect to remote resources not located on your home network.
VPNs offer many benefits, including total data encryption for all your connected applications, ad, malware, and tracker blocking, plus even mask your IP address. Using a VPN, you’re nearly untraceable online.
In the past, VPNs may have slowed Internet connections a little, but thanks to considerable improvements in VPN protocols, speeds are now faster than ever.
6. Protect your website
If you’re like me and run a one-person business from home, you’ll likely also be operating a website yourself. If that’s the case, be especially cautious about remotely administering your site. Not all web hosting providers have the same levels of security, and some can be real liabilities.
Where possible, opt for a web hosting provider that has more secure servers. An excellent way to observe this is to see if they work with external security providers like Sucuri to improve the protection offered to customers.
7. Keep your applications updated
Using personal devices for work at home can be dangerous. You need to ensure that all the applications you use are always updated to the newest versions. No software is perfect, and as time passes, developers often find security loopholes in their applications.
To address these loopholes, they issue software updates or patches. These aren’t always installed automatically, and in some cases, you need to download and run them separately to ensure your device is protected against the latest threats.
Remember that even your Operating System (OS) is an application, so make sure that’s kept updated as well!
8. Watch those passwords
Unless the IT department assigns us passwords, many of us tend to be somewhat lax about them. You aren’t the only one that thinks “123456” is a convenient password to use. The problem is that hackers know this as well and often try their luck with common password choices.
Always make sure you use complex passwords that are unique for each website or service they’re for. Where possible, keep passwords that meet the following guidelines:
- Combine upper and lowercase characters
- Include digits and special characters (such as @)
- Are at least 8 to 10 characters in length
If you have problems remembering your passwords, you can always use a password manager application like NordPass or LastPass. In addition, password managers can often help you keep payment details secure on your device.
9. Protect important documents
If you need to send out important documents, make sure you take steps to safeguard them. Encryption aside, you can also protect individual files such as PDFs. Adobe has a built-in password protection feature for its Reader application.
All you need to do is choose to password-protect the document in Adobe reader, and it can then be opened only by those you share the password with.
10. Enable multi-factor authentication where possible
Many services today support the use of Multi-factor Authentication (MFA). Enabling this means that you need an additional device to verify identity aside from login credentials like username and password. One example is the use of the Google Authenticator on smartphones.
MFA settings are usually located under “Security options” for the service that you are on. Not all services will offer the same type of MFA, so you will need to be prepared to use various means to secure the various ones used.
11. Enable remote wipe and device tracking
If any of your devices gets stolen, you want to find them or wipe the data off so it doesn’t fall into the wrong hands. Various applications can support this be it on a laptop or smartphone. Apple users can enable “Find My” in iCloud to see where their devices are. Android users can use Google’s Find My Device service to achieve the same thing.
For remote wipes, you’ll probably have to rely on a third-party service to handle that. Remember that you won’t be able to access the device physically, so some mechanism needs to fall into place if you lose the device.
Conclusion
As you can see, there are many ways of improving security to reduce the threat level to your home business. 20% of data loss incidents were reported due to negligence so don’t make the mistake of leaving things as they are.
Cyber threats today are more dangerous than ever. Cybercriminals aren’t just targeting businesses anymore; anyone that’s connected to the Internet is a potential victim.