Showing top 0 results 0 results found
Showing top 0 results 0 results found

If you’re a small business owner, it might be easy to take something like cybersecurity for granted. After all, why would a hacker spend time going after a small business when they can go after a multimillion-dollar company, right?
Unfortunately, for the vast majority of hackers, this is a numbers game, and unaware entrepreneurs are an easier target than companies with bigger budgets and cybersecurity teams.
Being part of the small business community has helped me see just how common these attacks are.
Not only can these hacks cost you time and money, but also damage your business’ reputation. Losing your customers’ personal or credit card information is never a good time.
Cyberattacks and WordPress vulnerabilities
One of the best ways to prevent cyberattacks is to create awareness and educate yourself in the cybersecurity landscape. In order to do this, let’s take a look at some of the most common cyberattacks and WordPress vulnerabilities.
Cross-site scripting (XSS)
This is when a script is injected into your website to send malicious code, which is typically used to grab cookie or session data. Cross-site scripting vulnerabilities are one of the most common ones found in WordPress plugins by a longshot, according to Wordfence.
Phishing
This is an attempt by attackers to obtain sensitive data, such as your passwords, credit card numbers, bank accounts, or other private information by sending an email pretending to be a trustworthy entity.
Man-in-the-Middle
This is when an attacker positions itself between you and the server to intercept your communication. This would be like your mailman opening up your bank statement, writing down your account details, resealing the envelope, and delivering it to your mailbox. This type of attack is most common in places with public WiFis like coffee shops and airports.
Malware
Short for malicious software, it is any software designed to cause damage to a computer, server, or network. Examples of malware include viruses, Trojans, and worms.
Backdoors
Backdoors are a piece of code, typically hidden in a file or plugin, that allows an attacker unauthorized and persistent access to your server. 71% of hacked websites end up with a backdoor left by the attacker, according to Sucuri.
Brute-force
This happens when an attacker continually guesses your password until the correct one is found.
Denial of Service (DoS)
A DoS vulnerability exploits errors and bugs in the code to overwhelm the memory of your website operating systems. Luckily, this type of attack is often used against big companies or very specific targets.
Now that we’ve looked at some of the most common cyberattacks and WordPress vulnerabilities, we can go over some tips to harden your WordPress security and protect your business so you can focus on other tasks like product creation and marketing.
1. Use a good WordPress host
While there are several plugins you can install to lock down your site, security is best done at the server level, which is what your WordPress host is responsible for.
Cheap shared hosting providers tend to overcrowd their servers to save on cost. Not only will this affect your website speed, but also your security. If someone out of the hundreds of users on your same server gets hacked, your site could be compromised as well.
Another issue is there could be someone sending out spam and getting the server IP blacklisted, which will affect your email deliverability. Lastly, these types of hosts often take a long time to update to the latest software and PHP, which introduces more vulnerabilities.
Ideally, you’d want to go for a managed host or one that includes advanced firewall features, intrusion detection and prevention systems (IDS and IPS), malware detection, and good support in case something does end up happening.
One budget-friendly and secure host I like using for my websites is NameHero. For my main business, however, I like using Cloudways.
2. Use a well-coded WordPress theme
When choosing a website theme, it’s super easy to go with something that looks good, however, just like web hosts, a poorly-coded WordPress theme can lead to low website speeds and security issues.
Common vulnerabilities in themes include things like XSS, SQL injections, and Cross-site Request Forgery (CSERF).
When choosing a theme, you want to go with a lightweight one that includes only the features you need. This is because the more code you have, the more processing your website does—which leads to lower speeds—and the higher the chances of introducing bugs and vulnerabilities.
You also want to make sure that the theme is constantly updated to keep up with new technology stacks and the team quickly fixes known vulnerabilities.
One way to check how active the developer and its team are is to google the name of your theme + “GitHub” and scroll down until you find the changelog. Here’s an example of the changelog from GeneratePress, which is the theme I use for all of my websites.
As you can see, the team is always working on introducing new features and fixing bugs.
3. Check and update your plugins
Plugins are the most common way websites get hacked. In fact, about 59.9% of hacked websites are compromised through plugin vulnerabilities, according to Wordfence.
Remember how I mentioned that if you’re in a shared hosting environment and one of your neighbors got hacked, you could be affected too? Well, if your neighbors use poorly-coded plugins or don’t update them regularly, their chances of getting hacked increase significantly.
Ideally, you’d want to install only the plugins you absolutely need and are updated regularly by their developers. One thing I like to do is check their support forum on WordPress.org to see if people are having issues or not.
For some WordPress plugins, you can enable auto-update. This is great for security but it can sometimes break your site if the update isn’t compatible with the current version of your theme. However, if your website theme is well-coded, auto-updates shouldn’t be an issue.
4. Don’t leave your laptop unattended
The coffee shop that I frequent the most to do my work doesn’t have a restroom inside. So whenever I need to use the restroom, I have to leave the coffee shop, walk to the adjacent building, get on the elevator, and go up to the third floor.
This whole routine gives someone plenty of time to install malware, look at my information, or steal my laptop. To prevent this from happening, I always leave some unimportant objects on the table (so I don’t lose my spot) and take my laptop with me.
I know it’s tempting to leave your laptop unattended if you’ll only be gone for a couple of minutes, but all an attacker needs is a few seconds to do some serious damage or steal your stuff.
Taking belonging with you wherever you go might seem a little obvious, but I see it happening all the time in coffee shops—at least where I live.
5. Use a VPN when connecting to unsecured networks
A few years ago, I used to travel a lot for work, which meant I had to frequently connect to public Wi-Fi networks in airports and hotels. The problem with these networks is that you’re more vulnerable to Man-in-the-Middle attacks.
As mentioned earlier, this is an attack where someone intercepts data sent from your computer to the server and from the server back to your computer.
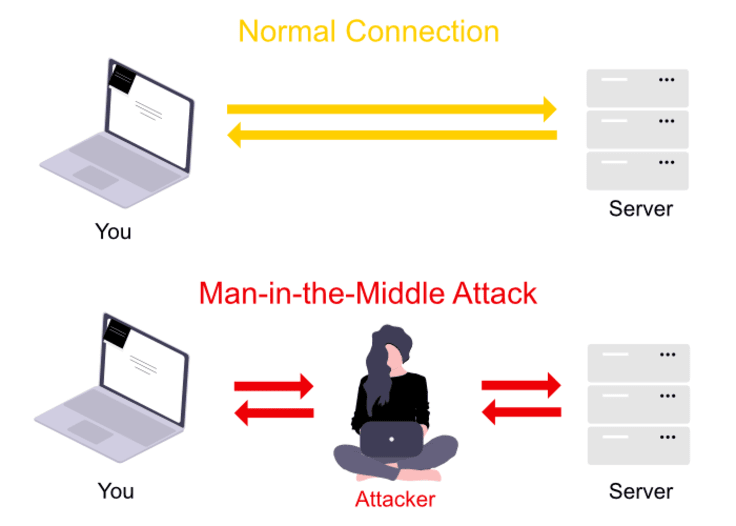
With these unsecured networks, attackers can also distribute malware and create fake connecting points for people to connect to.
A good way to prevent MitM attacks is to use a virtual private network (VPN) like NordVPN or ExpessVPN. A VPN creates a secure and encrypted tunnel between your device and the internet so that nobody can see what you’re up to.
6. Use full-disk encryption
As a business owner, you most likely have tons of sensitive information on your computer, such as bank accounts, business plans, and client data, that could affect your business if it got into the wrong hands.
Having someone steal your clients’ information can not only affect your business’ reputation but also lead to hefty fines or even jail time depending on the type of business you have. For example, a personal health information (PHI) leak can be a complete headache since the HIPAA and FINRA regulations are very strict.
Without full-disk encryption, anyone who gets a hold of your computer could access the data on your drive, even if you have a password protecting your login. With full-disk encryption, all the data will be encrypted, and be extremely difficult for attackers to decipher it.
Don’t worry, most operating systems like macOS and Windows come with full-disk encryption turned on by default. If for some reason, yours isn’t enabled, you can do so by following these steps.
macOS - Click the Apple logo on the top-left corner > System Preferences… > Security & Privacy > FileVault > click the lock icon on the bottom-left corner > type your password > Turn On FileVault.
Windows - Click the Start button > Settings > Update & Security > Device encryption > Turn on.
7. Create regular backups
Please, don’t wait until your website crashes or someone hacks you to start creating backups. Creating regular backups is a great way to easily recover from ransomware attacks—this is when an attacker encrypts your files and demands payment to restore access.
If you fall victim to a ransomware attack and currently have a backup in place, you can simply wipe everything clean and restore files and data from the backup.
Backups should be created for both your website and computer files.
WordPress - You can easily create backups using a free plugin like WPVivid or BackWPup. They have the option to create manual or scheduled off-site backups. Some web hosts also offer free backups, however, they’re often placed on the same server, so if something happens to the server, your backup will be gone. That’s why it’s often better to store them off-site.
macOS - Plug in your external drive > go to System Preferences > Time Machine > toggle the switch to On > Select Disk… > select the drive you connected > select “format as macOS Extended (journaled).”
Windows - Plug in your external drive > click Start > Settings > Update & Security > Backup > Add a drive > select the drive you connected.
Note: formatting your drive to “macOS Extended (journaled)” will erase all the files currently on the drive. However, the drive needs to be formatted to macOS Extended (journaled) to be used.
8. Use long and complex passwords
Surprisingly, one of the best ways to toughen up your website and accounts is to simply use long and complex passwords.
As a business owner, chances are you’re using Pinterest to drive traffic to your website, Instagram to build trust with your audience and sell products, separate bank accounts to manage your finances, and have so many other accounts that it’s sometimes tempting to just use the same easy password for everything, but that isn’t a good idea.
Here are the most popular passwords according to data gathered by NordPass.
- 123456
- 123456789
- picture1
- password
- 12345678
- 111111
- 123123
- 1234567890
- senha
- 1234567
- qwerty
- abc123
The longer and more complex the password, the harder it will be for an attacker to brute-force your account.
Ideally, your password should have more than 14 characters with a mix of uppercase, lowercase, numbers, and special characters.
You can use a free online tool like Strong Password Generator to create good passwords. Another option to create strong passwords and keep track of them is to use a free password manager like LastPass or 1Password.
9. Enable multi-factor authentication
Regardless of how complex your password is, there’s always a risk of someone discovering it.
Multi-factor authentication, also called two-factor authentication, is a security process in which you provide two different authentication factors to verify your identity.
The first method is typically your username and password and the second one a code that’s texted to your phone or a time-based one-time password (TOTP).
This is great because even if someone is able to crack your password, they’d still need your phone to access your accounts.
Most applications nowadays have the option to enable multi-factor authentication, so make sure that you do so for important accounts, such as your bank account.
When it comes to protecting your WordPress site, however, you’ll have to install a free plugin like Two Factor Authentication or Google Authenticator to add the multi-factor authentication functionality.
It takes several years to build a reputation and one security breach to ruin it
While some of these hardening techniques, such as using a strong password, might look simple and easy to implement, they’re extremely powerful and will make a huge difference in protecting your business and website from hackers.
As Chris Pirillo once said, “Passwords are like underwear: don’t let people see it, change it very often, and you shouldn’t share it with strangers.”
For most of you reading this, your website is your business and income, so it’s important to take some time to implement some (or all!) of the security best practices mentioned above.
Stay safe, my friend!